
Menace actors are spoofing AI chatbots and answer suppliers to distribute ransomware, Cisco Talos revealed on Thursday. The menace intelligence analysis staff detailed three notable threats: CyberLock, Lucky_Gh0$t, and a brand new malware they named Numero.
All three discover victims by pretend installers for AI providers, which the menace actors push to the highest of search outcomes by gaming web optimization.
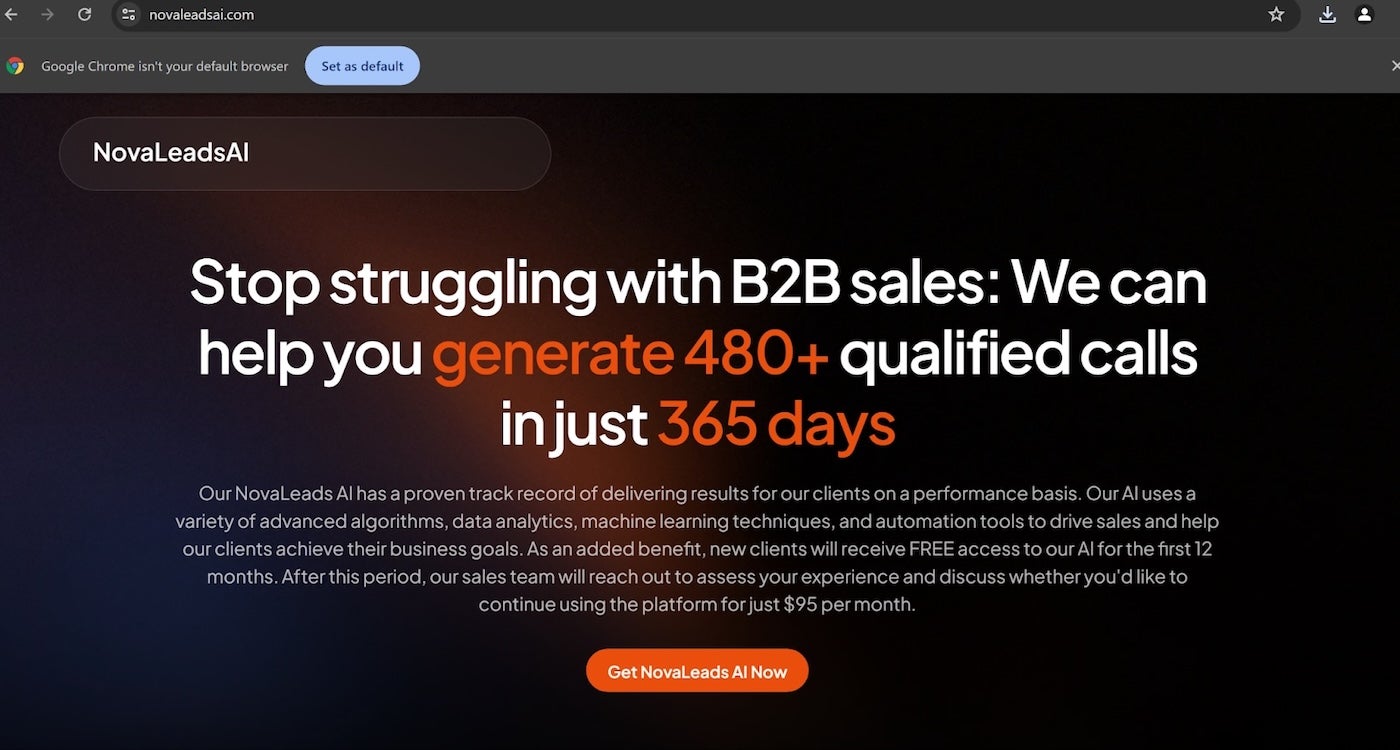
Cyberlock hides behind a pretend website that appears like NovaLeadsAI
One malicious URL spoofed NovaLeadsAI, a service for business-to-business gross sales. The menace actors used a .com top-level area as an alternative of the .app top-level area utilized by the actual website. As a result of the menace actors manipulated web optimization practices, the pretend web site was more likely to seem within the prime search outcomes for associated phrases in serps.
The menace actors use a ransomware pressure known as CyberLock, which encrypts particular recordsdata on the consumer’s gadget,” Cisco Talos stated in an announcement. “If their gadget is contaminated, the consumer will see a message demanding a ransom in trade for the return of their “delicate enterprise paperwork, private recordsdata and confidential databases.”
The menace actor set the ransom at $50,000, paid in Monero cryptocurrency. So as to add a psychological aspect, they falsely claimed the cash can be used for humanitarian support in locations comparable to Palestine, Ukraine, Africa, and Asia. The menace actor’s sample of assault included threatening to reveal the locked paperwork, though Cisco Talos discovered no proof the ransomware code included the performance to take action.
SEE: Menace actors planted hidden prompts within the GitLab Duo AI assistant to steer it towards phishing hyperlinks and pretend URLs.
LuckyGhost hides inside a ‘ChatGPT installer’
The LuckyGhost ransomware disguises itself as a obtain for a so-called full model of ChatGPT, particularly a file named “ChatGPT 4.0 full model – Premium.exe.” The true ChatGPT chatbot might be accessed on-line at no cost. The LuckyGhost bundle consists of the ransomware executable and a few open-source Microsoft instruments for working with AI in Azure.
If put in, LuckyGhost locks up recordsdata of varied sorts, together with Microsoft Workplace and Adobe content material, media and pictures, and backup and database recordsdata.
Numero spoofs on-line platform InVideo AI
One other malware, often known as Numero, masquerades as the net platform InVideo AI. Numero prompts the consumer to obtain a malicious file, utilizing the InVideo AI identify within the file’s metadata. If put in, the pretend installer deposits an executable known as ‘wintitle.exe’, a malicious Home windows batch file, and a VB script onto the gadget. Cisco Talos supplied indicators of compromise in a GitHub repository.
These malware strains function a reminder to be cautious of hyperlinks — particularly product listings on the prime of search engine outcomes — and to totally look at URLs, web sites, and apps earlier than downloading any recordsdata.
“Organizations and customers should train excessive warning, meticulously confirm sources, and rely completely on respected distributors to keep away from falling prey to those threats,” cybersecurity researcher Chetan Raghuprasad wrote in a weblog submit.